NST Cyber Launches CTI Dashboards Offering Weekly Remote Vulnerability Exploitation Insights
NST Cyber Launches CTI Dashboards Offering Weekly Remote Vulnerability Exploitation Insights for Information Security Leaders
SAN JOSE, CA, UNITED STATES, January 16, 2025 /EINPresswire.com/ -- NST Cyber, the leading innovator in Continuous Threat Exposure Assessment and Adversary Validation, has launched two new live Cyber Threat Intelligence (CTI) dashboards to deliver the latest insights based on exploitation intelligence. As a cybersecurity community initiative tailored for CISOs and information security leaders, these dashboards offer actionable intelligence on external remote vulnerabilities and adversarial tactics targeting internet-facing enterprise assets.Bringing Weekly Exploitation Intelligence to CISOs
The CTI dashboards address the critical need for proactive security measures, providing up-to-date data and trends to empower security leaders with the knowledge required to prioritize vulnerabilities and protect against evolving threats.
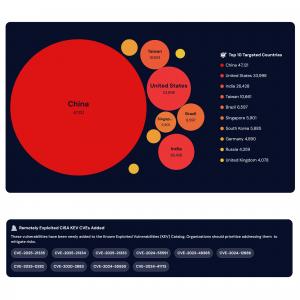
Enterprise Exploitation Trends Dashboard
The Enterprise Exploitation Trends Dashboard provides a strategic view of weekly exploitation intelligence, enabling CISOs and security teams to take informed action on vulnerabilities affecting enterprise vendors and products.
Use Cases and Key Features
• Real-Time Trend Monitoring: Up-to-date insights into active external vulnerability exploitation help organizations anticipate threats before they escalate.
• Risk-Based Prioritization: Data-driven insights enable security leaders to prioritize patching and mitigation strategies for the most critical vulnerabilities, reducing potential attack surfaces.
• Adversarial Alignment Analytics: Highlights how exploitation trends align with known adversarial techniques, offering the context needed to reinforce defensive strategies.
• Proactive Threat Defense: Ideal for enterprise environments, helping organizations understand the exploitability of vendor-specific vulnerabilities to maintain operational security.
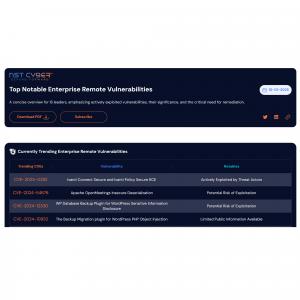
Threat Exposure Management Bytes Dashboard
The Threat Exposure Management Bytes Dashboard focuses on delivering actionable intelligence about the most actively exploited external remote vulnerabilities from the past week, ensuring security teams stay ahead of emerging threats.
Use Cases and Key Features
• Weekly High-Severity Insights: A curated list of trending vulnerabilities, focusing on those most likely to impact internet-facing assets.
• Actionable Risk Mitigation: Tailored recommendations for addressing high-risk exposures enable organizations to respond quickly and effectively.
• Adversary Validation for Preparedness: Provides insights that simulate real-world attack scenarios, helping organizations validate the effectiveness of their security controls.
• Incident Response Enablement: Helps security teams refine their incident response strategies by focusing on vulnerabilities actively targeted by adversaries, ensuring better preparedness for emerging attack campaigns.
Enhancing Resilience with Actionable Intelligence
“These dashboards cater to organizations looking to enhance their external threat visibility, prioritize critical vulnerabilities, and validate security controls against real-world exploitation scenarios,” said Babu Rao Kittur, Senior Technical Delivery Manager at NST Cyber, the organization behind NST Assure. “By integrating these insights into operational workflows, CISOs and security leaders can strengthen their organizations’ resilience against sophisticated cyber threats.”
Access the Dashboards Today
The Enterprise Exploitation Trends Dashboard and Threat Exposure Management Bytes Dashboard are now live and accessible on the NST Cyber website. Visit https://www.nstcyber.ai to explore weekly exploitation insights, download reports, or subscribe for regular updates.
About NST Cyber
NST Cyber specializes in Continuous Threat Exposure Assessment and Adversary Validation, offering cutting-edge solutions to predict, validate, and mitigate risks from external vulnerabilities. By delivering actionable intelligence and fostering proactive security measures, NST Cyber helps organizations defend against evolving cyber threats.
PR Team
NST Cyber
+91 99956 90211
info@nstcyber.ai
Visit us on social media:
LinkedIn
Distribution channels: Banking, Finance & Investment Industry, Companies, IT Industry, International Organizations, Technology
Legal Disclaimer:
EIN Presswire provides this news content "as is" without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the author above.
Submit your press release